Trust Wallet Browser Extension Exploit: $7 Million Stolen, Binance CZ Pledges Full Compensation
A critical security vulnerability within Trust Wallet’s browser extension v2.68 has resulted in the theft of approximately $7 million in user funds. In a decisive response, Binance founder Changpeng Zhao (CZ) has confirmed that Trust Wallet will fully compensate all affected users for their losses. Users still operating on the compromised version are strongly urged to take immediate measures to secure their digital assets.
The sophisticated exploit reportedly unfolded around Christmas Day, though intelligence suggests the malicious planning began as early as the start of December. Cybersecurity firm SlowMist further revealed that these compromised extensions were not only facilitating the theft of funds but also actively exfiltrating users’ sensitive personal information.
Trust Wallet officially acknowledged the incident via a post on X (formerly Twitter), confirming that its browser extension version 2.68 was impacted, primarily affecting desktop users. The immediate recommendation issued by the official team is to upgrade promptly to version 2.69.
CZ Confirms Full Reimbursement and Ongoing Investigation
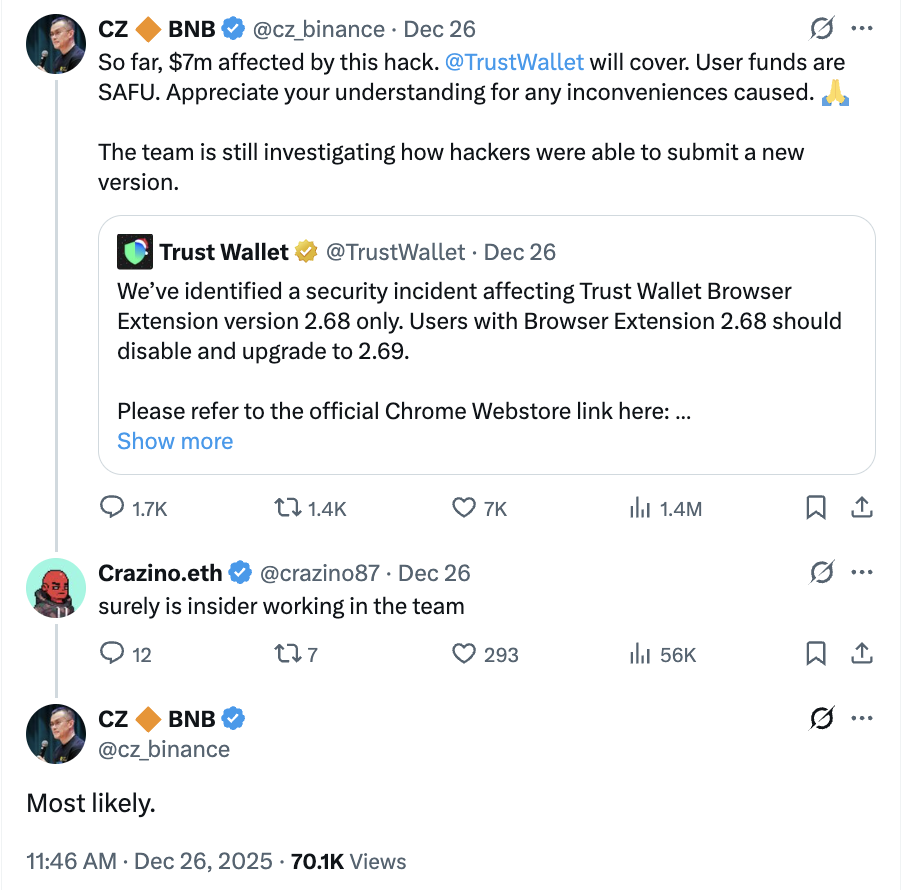
Binance co-founder CZ took to X on Friday to provide reassurance to the crypto community, stating, “So far, $7m affected by this hack. @TrustWallet will cover. User funds are SAFU. Appreciate your understanding for any inconveniences caused. 🙏 The team is still investigating how hackers were able to submit a new version.” This commitment underscores Trust Wallet’s dedication to user security and trust in the wake of the breach.
So far, $7m affected by this hack. @TrustWallet will cover. User funds are SAFU. Appreciate your understanding for any inconveniences caused. 🙏
The team is still investigating how hackers were able to submit a new version. https://t.co/xdPGwwDU8b
— CZ 🔶 BNB (@cz_binance) December 26, 2025
The Growing Threat of Crypto Wallet Exploits
The Trust Wallet incident serves as a stark reminder of the escalating security risks faced by digital asset investors. Data from Chainalysis reveals a concerning trend: over $3.4 billion was stolen in 2025 alone, with a single Bybit incident in February accounting for approximately $1.5 billion. While the total value stolen from individual wallets in 2025 ($713 million) saw a decrease compared to 2024, the sheer number of individual wallet theft incidents surged to 158,000, impacting 80,000 unique victims.
Expert Analysis Uncovers Sophisticated Backdoor and Insider Suspicions
Blockchain security firm SlowMist, through its founder Yu Xian, provided crucial insights into the attack’s timeline and methodology. Yu Xian’s observations indicate that the orchestrators of the Trust Wallet attack began their preparations as early as December 8.
Trust Wallet 浏览器扩展带后门版本是 2.68.0,修复后的是 2.69.0,对比了下,正常代码和后门代码的代码差异,如图。
后门代码增加了个 PostHog 来采集钱包用户的各种隐私信息(包括助记词),并发送到攻击者服务器 api.metrics-trustwallet[.]com 。
预估时间线:攻击者至少 12.8… https://t.co/EpvCqRli7n pic.twitter.com/FOLjD6aPar
— Cos(余弦)😶🌫️ (@evilcos) December 26, 2025
Comparing the compromised version 2.68.0 with the patched 2.69.0, Yu Xian detailed the malicious code. He explained, “The backdoor code added a PostHog to collect various private information (including seed phrases) from wallet users and send it to the attacker’s server api.metrics-trustwallet[.]com.” The estimated timeline further solidifies the sophistication of the attack: “attackers started preparations at least on 12.8, successfully planted the backdoor on 12.22, began transferring funds on Christmas Day 12.25, and were then discovered.”
Adding another layer of concern, some industry observers have posited that the exploit bears hallmarks of potential insider activity. The ability of attackers to successfully submit a new, compromised version of the Trust Wallet extension to the platform raises significant questions. As one insider noted, “This ‘hack’ is not natural. The possibility of an insider being involved is high.”
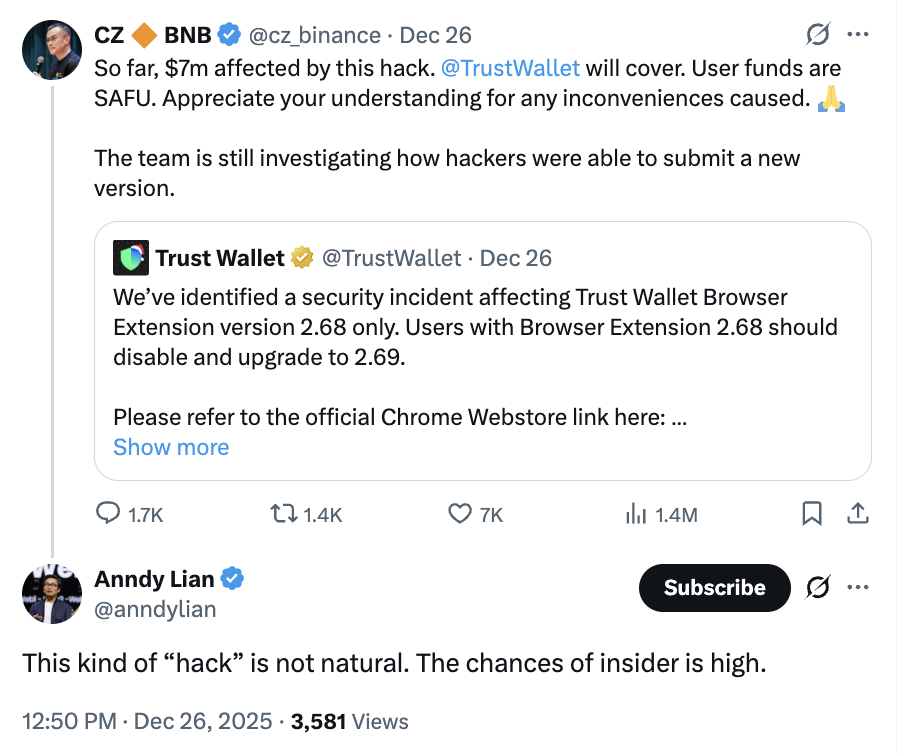
Interestingly, CZ himself acknowledged the possibility of internal involvement when confronted with community speculation. SlowMist further supported this theory, highlighting that the attackers demonstrated an “intimate familiarity with the Trust Wallet extension’s source code,” which was critical for implementing the backdoor capable of harvesting sensitive user data.
Disclaimer: This article is provided for market information purposes only. All content and views are for reference only and do not constitute investment advice, nor do they represent the views and positions of BlockTempo. Investors should make their own decisions and transactions. The author and BlockTempo will not bear any responsibility for direct or indirect losses resulting from investor transactions.





