Author: Frank, PANews
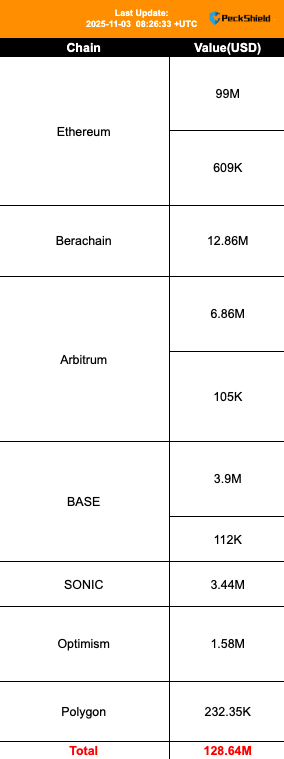
A seismic event rocked the DeFi landscape on November 3rd, as veteran protocol Balancer’s treasury address witnessed an unprecedented outflow of funds. What began as an initial report of $70 million in compromised assets rapidly escalated, climbing to $116.6 million, and finally settling at a staggering $128.64 million. This colossal breach not only devastated Balancer but also exposed a systemic vulnerability across its ecosystem, putting 27 “fork” protocols built on Balancer V2 at significant risk.
Balancer V2 Suffers $128 Million Exploit
On November 3rd, blockchain security firm PeckShield first detected unusual transfers from Balancer V2’s treasury. Significant amounts of Wrapped Ether (WETH) and liquid staking derivatives like wstETH and osETH were siphoned into a newly created wallet. The Balancer team swiftly confirmed an on-chain attack, with continuous monitoring eventually tallying the total losses at a staggering $128 million. Critically, the team clarified that the exploit was confined exclusively to V2 Composable Stable Pools, assuring users that the newer V3 architecture and other V2 pool types, such as Weighted Pools, remained secure.
While Balancer’s team had yet to disclose the precise root cause by November 4th, on-chain analysts at Nansen pinpointed a “faulty access-control check” as the core vulnerability. The attacker ingeniously exploited the V2 protocol’s manageUserBalance function. By submitting a maliciously crafted instruction, they tricked the protocol’s internal ledger into registering a substantial “fee” that was then attributed to the attacker’s ownership. Subsequently, the attacker initiated standard withdrawal requests, transferring the vast sum of assets directly into their controlled accounts. This wasn’t a display of advanced cryptographic prowess but rather a sophisticated exploitation of a logical flaw within the protocol. Some analysts speculate, based on console logs left by the perpetrator, that the attacker might have leveraged AI models to aid in code review and exploit discovery, pinpointing a critical oversight missed by multiple auditors.
Systemic Risk: 27 Fork Protocols Affected, Chains Implement Emergency Measures
Beyond the attacker’s cunning, the industry grappled with profound disappointment: Balancer V2, a protocol that had undergone a remarkable 11 audits by four leading security firms—OpenZeppelin, Trail of Bits, Certora, and ABDK—still harbored this critical vulnerability. The irony is particularly sharp given that the “Composable Stable Pool,” the specific component exploited, received dedicated audits from Certora and Trail of Bits as recently as September 2022.
As a battle-tested DeFi protocol operating for years, Balancer V2 has spawned a vast ecosystem of 27 “fork protocols.” These derivative projects, by design, inherited the very same logical flaw present in the original Balancer V2 code. For the attacker, this vulnerability was akin to a master key, capable of unlocking the treasuries of all these similarly flawed “fork” protocols.
The fallout from this exploit was far-reaching, impacting multiple blockchains. Ethereum mainnet’s Balancer V2 bore the brunt of the attack, with an estimated $100 million in losses. Berachain’s BEX protocol faced significant damage, potentially losing $12.86 million. In total, seven public chains, including Arbitrum, Base, and Sonic, saw protocols affected.
This unforeseen calamity forced the industry into a difficult ethical dilemma: should they uphold the purist “code is law” decentralization ethos, allowing user funds to be irrevocably lost? Or should they implement centralized interventions to safeguard users?
Berachain, facing the most severe impact, made the most radical and controversial decision: coordinating its validators to temporarily halt the entire network. Through a transaction rollback, Berachain successfully rescued over $12 million in assets at risk on its BEX exchange. This move, while effective, sparked intense debate within the community. Critics questioned whether such an action fundamentally undermined the chain’s finality and security, arguing it made the network resemble a private chain more than a public blockchain. Smokey the Bera, an anonymous co-founder of Berachain, responded, “I think your concerns are valid, but I believe extraordinary circumstances require extraordinary measures – we’ve seen similar approaches in cases like Sui and Hyperliquid in the past.” The majority of the community, however, largely supported the decision, acknowledging that the catastrophic impact of massive fund losses far outweighed the adherence to an abstract “decentralization” ideal.
Other chains adopted different emergency strategies. The Sonic chain activated an “on-chain account freezing mechanism,” locking the attacker’s wallet and its $3.4 million in funds without halting network operations. Polygon validators, meanwhile, proactively began “censoring” transactions originating from the attacker’s address.
Repeated Vulnerabilities Lead to TVL Halving and a Crisis of Trust
Balancer’s operational history has, unfortunately, been a continuous battle against complex logical vulnerabilities. The protocol has endured multiple hacks, with at least five significant incidents recorded between 2020 and 2025. These attacks ranged from early flash loan exploits to more sophisticated vulnerabilities targeting V2 enhanced pools.
However, past incidents typically resulted in losses ranging from hundreds of thousands to a maximum of $2 million. For Balancer, these prior breaches were often perceived as opportunities to patch vulnerabilities and strengthen the protocol. This latest catastrophic exploit, with estimated losses exceeding $100 million, has irrevocably shattered market confidence and trust in Balancer.
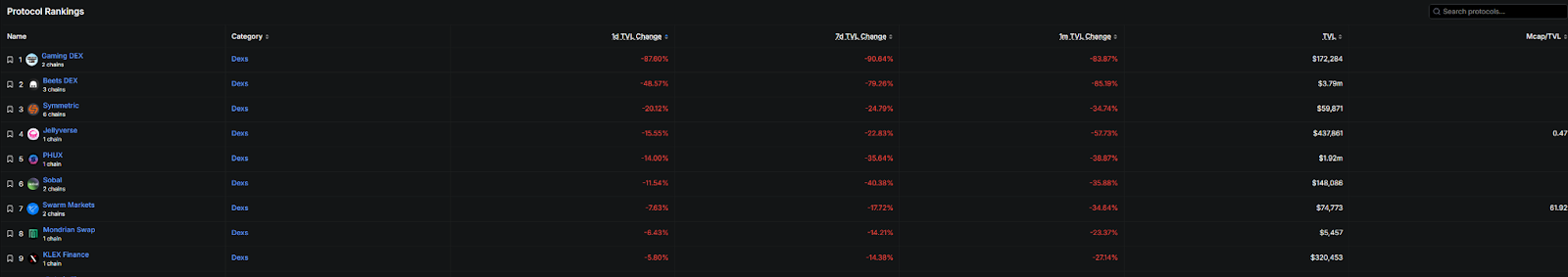
Data from DefiLlama paints a grim picture: immediately following the attack, Balancer’s Total Value Locked (TVL) plummeted from $776 million to $345 million, representing a more than 50% reduction. Balancer V2 alone saw its TVL decrease by $230 million. Fork protocols built on Balancer V2 also experienced a mass exodus of funds, with Gaming DEX’s TVL dropping by a staggering 87% in a single day, and Beets DEX declining by 48%.
Even unaffected protocols like Lido publicly announced the withdrawal of their Balancer positions as a precautionary measure, despite their funds not being directly compromised. Similarly, fork protocols such as Gaming DEX, while confirming no actual impact, opted to remove the majority of their liquidity out of an abundance of caution.
For any DeFi protocol, trust is paramount, far more valuable than gold, especially when operating with a history of recurrent security breaches. As of November 4th, official reports indicate that StakeWise DAO successfully recovered over $20 million of the stolen funds through a multisig contract call, reducing the total outstanding loss to $98 million. The attacker’s assets remain in flux, with more than half already converted into ETH.
The $128 Million Exploit: A Costly Lesson and Uncomfortable Questions for DeFi
The $128 million Balancer exploit serves as an incredibly expensive, yet perhaps necessary, lesson in the ongoing evolution of decentralized finance. It forces the industry to confront three piercing questions:
- The Efficacy of Audits: When a “gold standard” of 11 comprehensive audits fails to uncover a critical vulnerability lurking for two years, what is the true meaning and reliability of smart contract auditing?
- Composability: Innovation or Curse? If a fundamental protocol’s flaw can instantly compromise 27 derivative protocols, becoming a “code contagion,” is DeFi’s much-lauded composability a driver of innovation or a systemic curse?
- Decentralization vs. Pragmatism: When emerging public chains are compelled to choose between the ideals of “decentralization” and the imperative to “save users,” has the “code is law” philosophy given way to a more “pragmatic centralization”?
Moving forward, DeFi security cannot solely rely on an increasing number of audits. It must pivot towards simpler, more robust protocol designs that inherently reduce the attack surface. For the countless users who lost trust and capital in this incident, the cost of this collective realization is undeniably steep.
(The above content is an authorized excerpt and reproduction from our partner PANews. Original article link)
Disclaimer: This article is for market information purposes only. All content and views are for reference only and do not constitute investment advice. They do not represent the views and positions of BlockTempo. Investors should make their own decisions and trades. The author and BlockTempo will not bear any responsibility for direct or indirect losses incurred by investors’ transactions.